

BUSINESS VALUE
Boost prevention
capabilities
Increases security
efficiency
Increases endpoint
performance
Eliminate cost and
burden associated with
keeping up-to-date
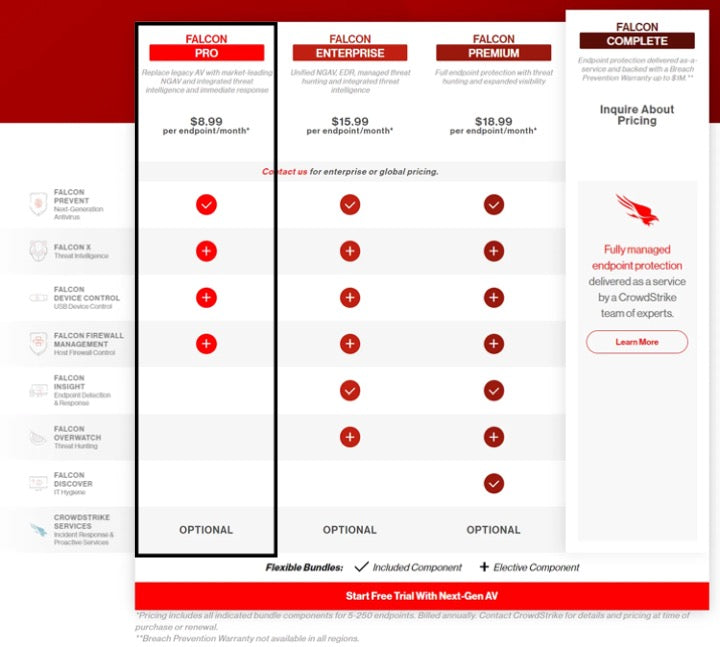
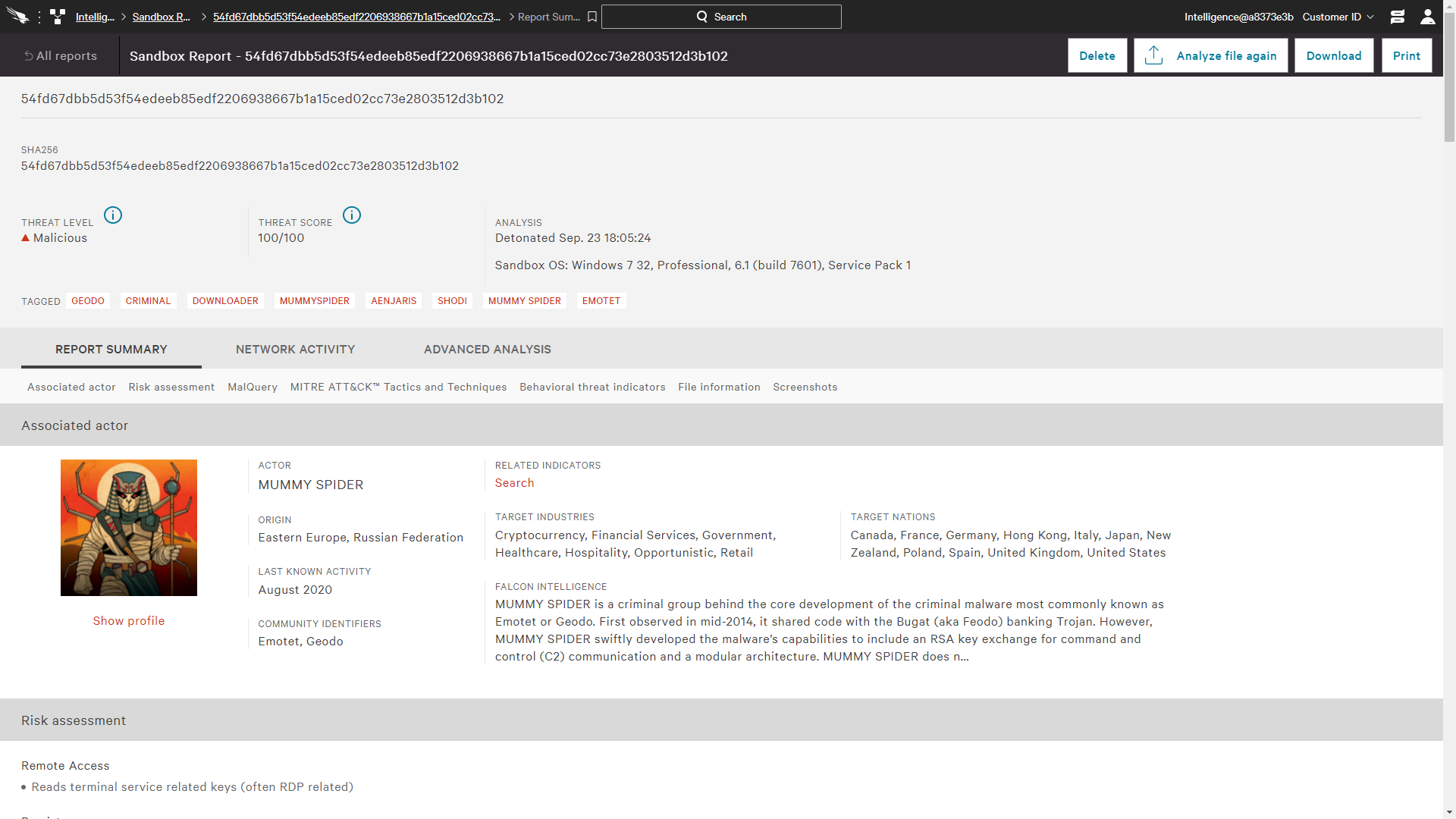
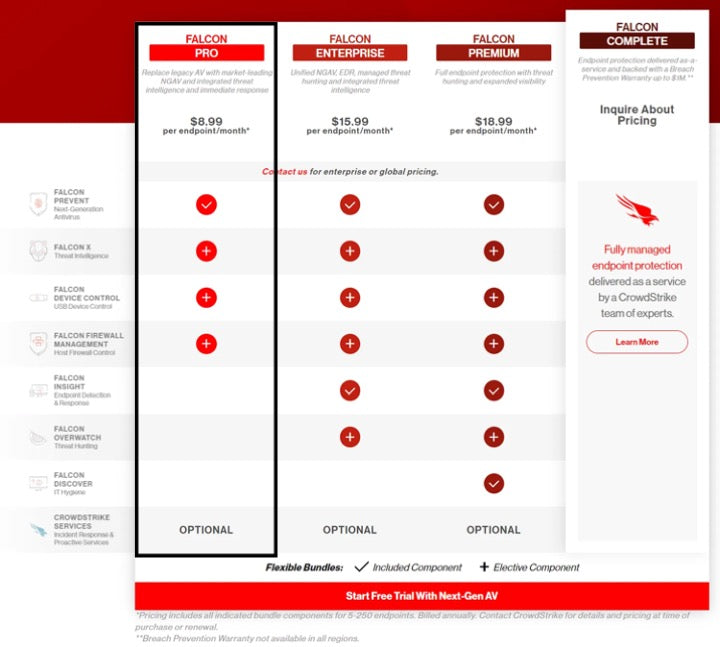
MODULES INCLUDE

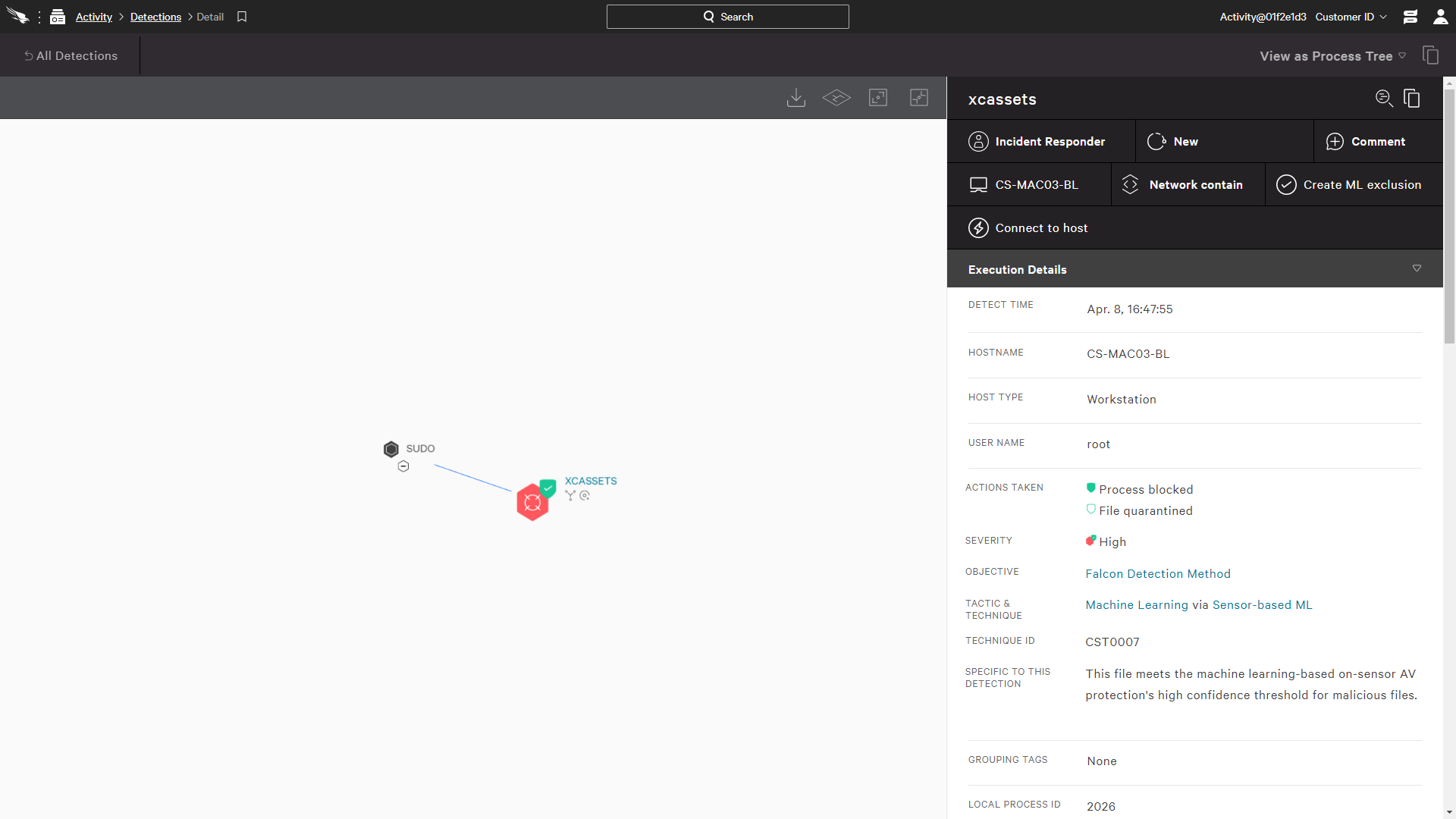
FALCON PREVENT
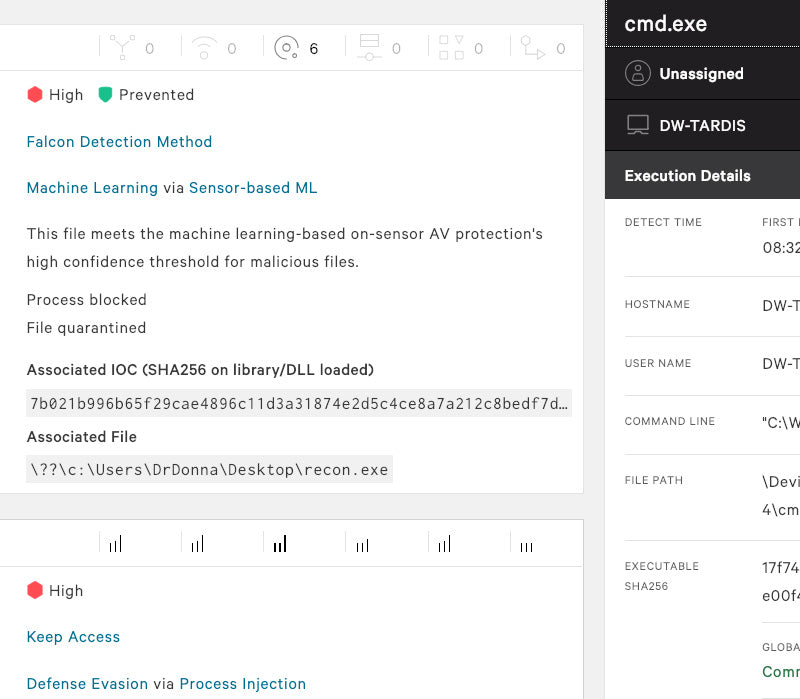
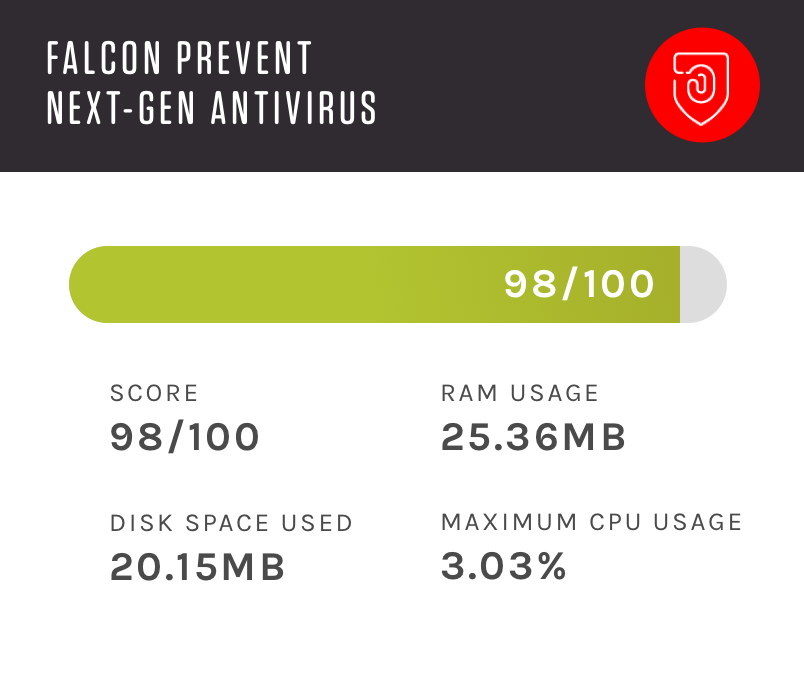
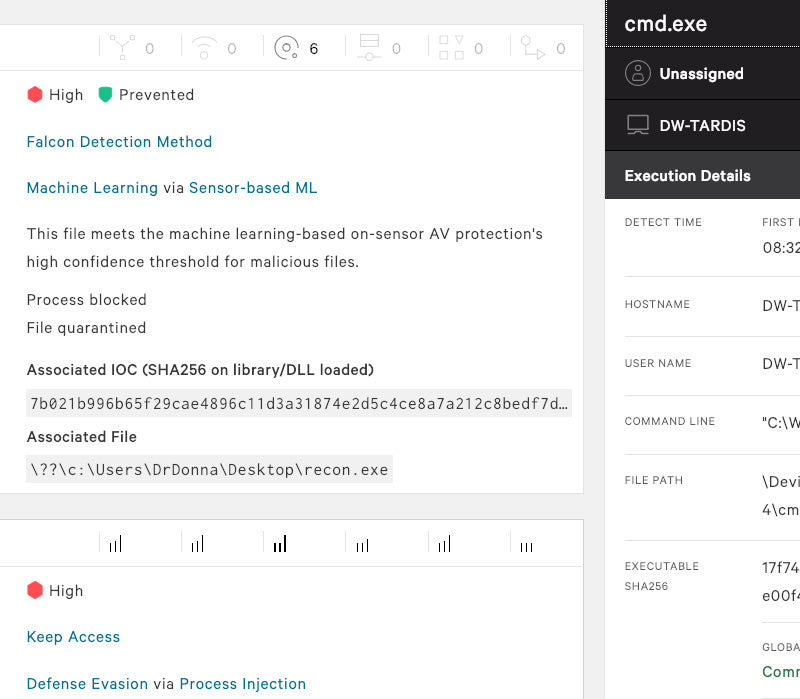
Protects against both malware and malware-free attacks; third-party tested and certified, allowing organizations to confidently replace their existing legacy AV

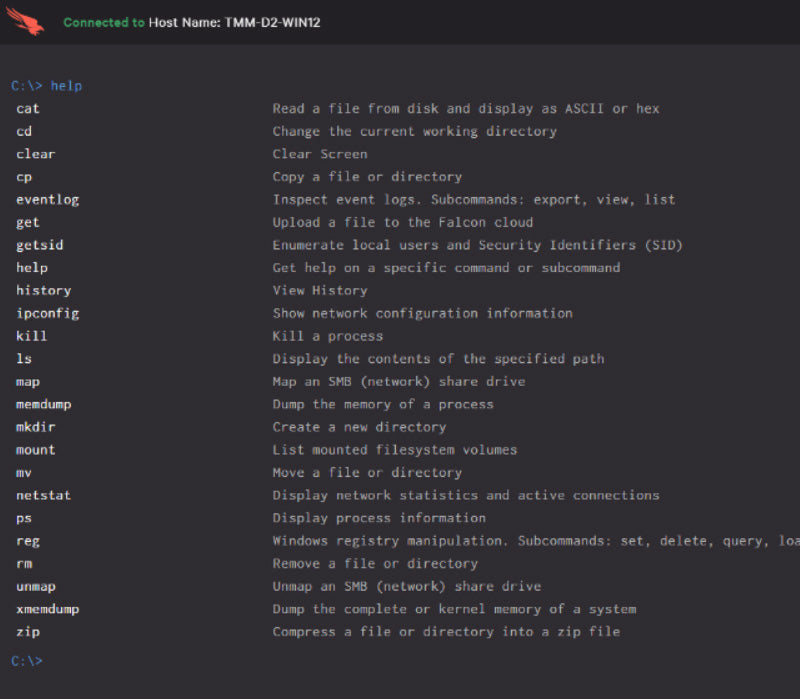
FALCON INTELLIGENCE
Integrates threat intelligence into endpoint protection, automating incident investigations and speeding breach response

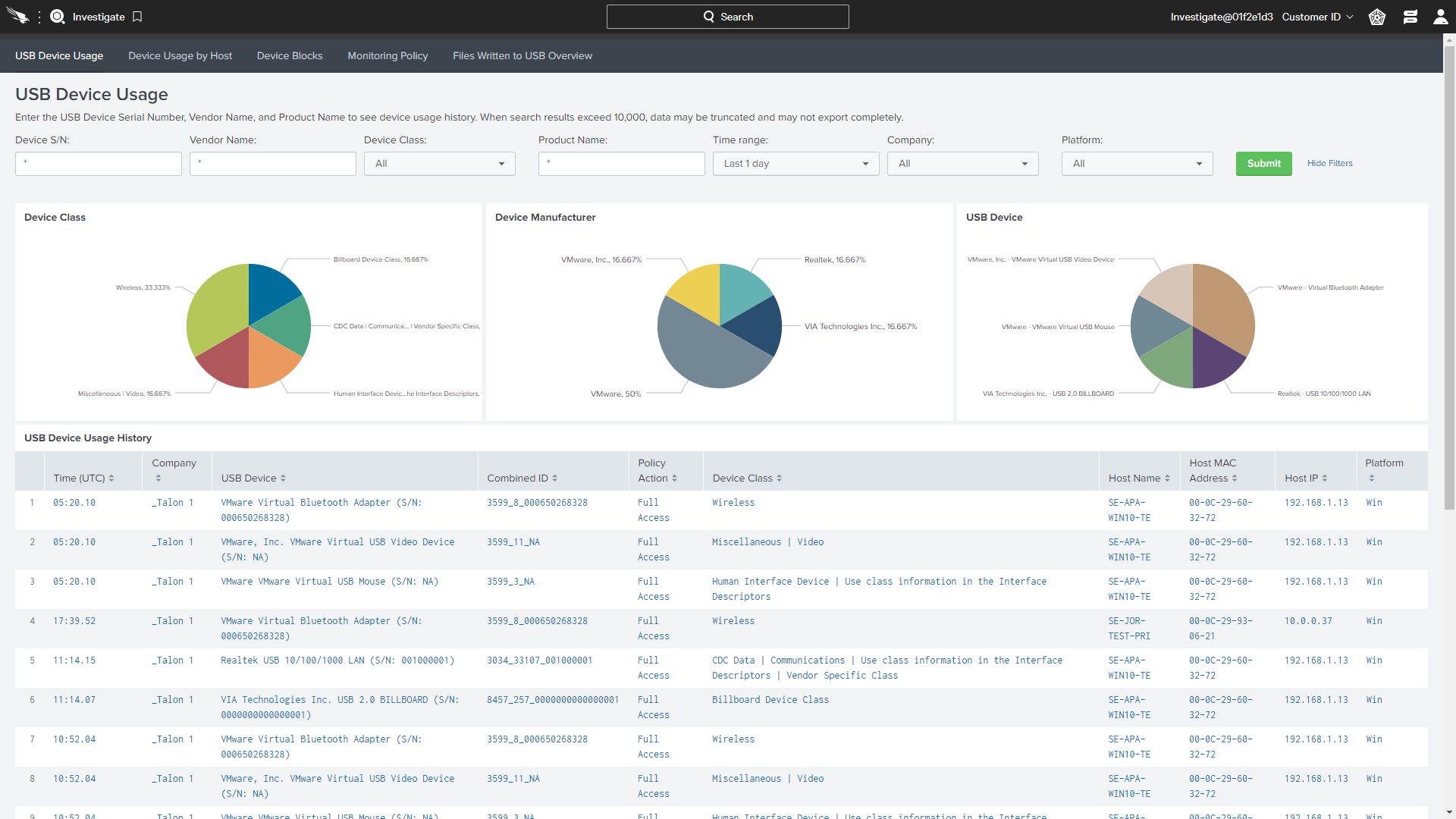
FALCON DEVICE CONTROL
Enable safe and accountable USB device usage with effortless visibility and precise and granular control of USB device utilization

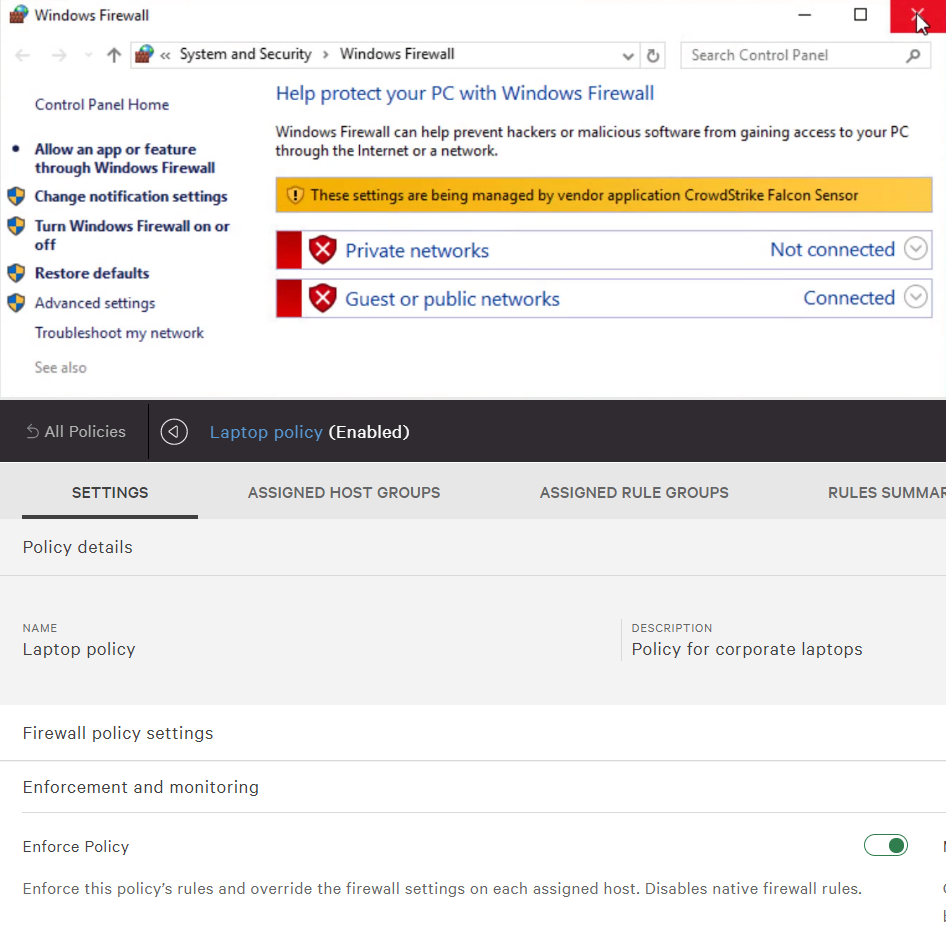
Falcon Firewall Management
Provides simple, centralized firewall management, making it easy to manage and enforce host firewall policies
About Defensive
Defensive is a Next Generation Solution Provider for a Cloud-First World. We exist to take the guesswork out of Cybersecurity and Information Technology procurement and adoption.
Defensive of your Brand.
Trusted by leading enterprises around the globe.
Defensive of your People.
Let’s create harmony between Infosec, IT, Executives, End Users, and Finance.
Defensive of your Time.
We’re straight to the point, with technologies and strategies that work.
Defensive of your Budget.
Eliminate wasted expenditure and maximize the value of every dollar.
TRUSTED BY
87 of the Fortune 1000
Over 1,400+ small, medium and large enterprises.



As Seen In